Due to perfectly legit circumstances, let's say suspicion of malware, I wanted to take a peek under the hood of an app running on my android device. It was apparantly exchanging data with a webservice, and my goal was to figure out what, where and how.
Here are the steps i followed to take a peek at the source code, on my unrooted phone. There is probably obfuscation and other security measures out there I haven't encountered yet, so your mileage may vary wildly.
1) Android apps are packaged as single .APK file. To grab it, I used
ASTRO File Manager which lets you back up applications. It dumped an .APK file on the sdcard, which i transferred to my desktop.
2) Your APK file contains a .dex file (
Dalvik executable). Download
dex2jar, and run it on your APK (dex2jar.bat your.application.apk). This should produce a .JAR file.
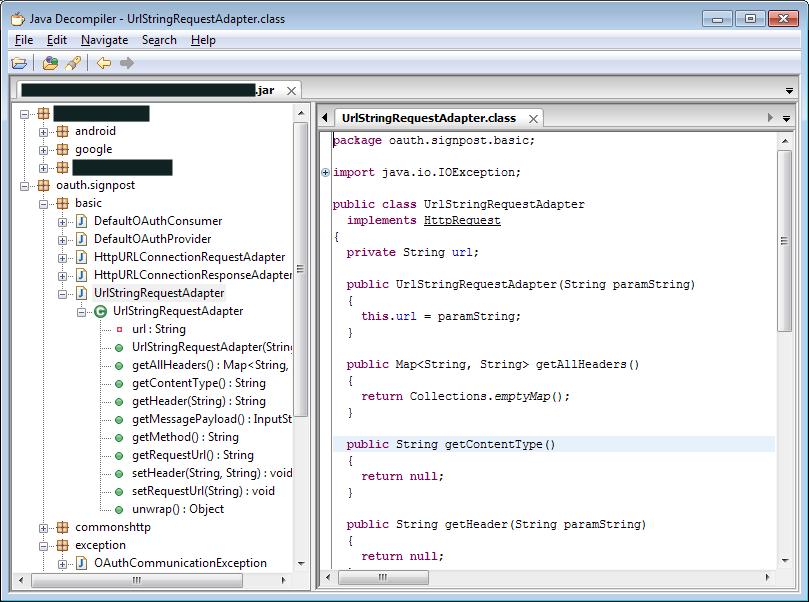
3) Download another tool:
JD-GUI, a lovely graphical java decompiler. Run it and open your .JAR file.
Boom: